2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
According to recent statistics, $4.1 billion was lost to decentralized finance (DeFi) hacks in 2024 alone. This alarming figure highlights the critical need for robust security measures in the blockchain sector, particularly for cryptocurrency platforms. In this comprehensive guide, we’ll delve into one of the most essential frameworks for ensuring optimal security in the crypto space: HIBT analysis.
Understanding HIBT Analysis
HIBT, an acronym standing for Human, Infrastructure, Blockchain, and Technology, is a multi-faceted approach to assessing and enhancing the security of digital assets. Utilizing HIBT analysis allows crypto platforms like hibt.com to identify vulnerabilities within their operations and implement remediation strategies effectively.
Breaking Down HIBT Components
- Human: The role of individuals in security practices. User training is often the first line of defense.
- Infrastructure: This encompasses the hardware and software environments that host blockchain technologies.
- Blockchain: Analyzing the specific features of the blockchain in use, such as consensus mechanisms.
- Technology: Tools and platforms that support the blockchain eco-system.
The Importance of Blockchain Security Standards in 2025
As we approach 2025, the demand for enhanced blockchain security is more pressing than ever, especially in regions with burgeoning crypto markets like Vietnam. Recent studies suggest that the number of crypto users in Vietnam has surged by over 300% in 2024, emphasizing the need for stringent security protocols.

This rise in crypto adoption calls for a meticulous approach to security, centered around integrating HIBT analysis into mainstream practices. Here’s what that would involve:
Consensus Mechanism Vulnerabilities
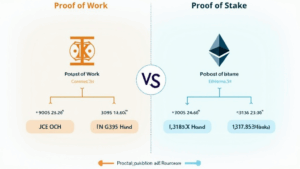
Let’s break it down: blockchain networks rely on consensus mechanisms, such as Proof of Work or Proof of Stake, to validate transactions. Each carries its unique vulnerabilities.
- Proof of Work is susceptible to 51% attacks, allowing a malicious actor to control network consensus.
- Proof of Stake may lead to centralization issues if fewer entities hold a majority of stakes, thus posing risks.
Implementing thorough HIBT analysis on consensus mechanisms can optimize these vulnerabilities and bolster network security.
Case Study from Vietnam
Using Vietnam as a case study: According to local surveys, security breaches have cost the Vietnamese crypto market around $1 billion in losses over the past year. To counter this, platforms should consider adopting a comprehensive HIBT analysis framework.
Best Practices for Conducting HIBT Analysis
Conducting an effective HIBT analysis involves various strategies:
- Regular audits of human resources to ensure adequate training.
- Assessment of physical infrastructure and protocols in place for data protection.
- Blockchain technology assessment to identify outdated code or protocols.
- Implementation of cutting-edge technology solutions that enhance security.
For example, the application of multi-signature wallets can reduce security risks by requiring multiple approvals before executing transactions.
Integrating HIBT Analysis for Future-proofing Crypto Platforms
As the digital landscape evolves, so must security measures. Future-proofing involves adopting innovative practices that anticipate and mitigate risks. A focus on HIBT analysis helps platforms to:
- Enhance overall security posture.
- Follow the newest industry regulations as they emerge.
- Educate users about security risks and practices.
Final Thoughts on the HIBT Framework
Integrating HIBT analysis into a crypto platform’s security infrastructure not only mitigates risks but also builds user trust in an increasingly competitive market. By continually evaluating human, infrastructure, blockchain, and technology aspects, platforms can safeguard digital assets effectively against threats.
In conclusion, adapting to the 2025 landscape of blockchain security is essential. With the right measures, crypto platforms can thrive in both local and global markets, particularly as seen in growth trends like Vietnam’s.,bitcoincashblender is committed to implementing these standards.
Expert Author: Dr. Alexander Moore, a blockchain technology consultant with over 15 publications in cybersecurity and blockchain audits, has led significant projects in enhancing security for leading financial institutions.