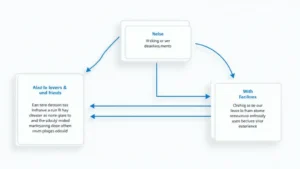
Leading HIBT Security Audit Methodology for Crypto Platforms
In 2024, the cryptocurrency landscape witnessed a staggering $4.1 billion in losses due to various hacks, making HIBT security audit methodology more vital than ever. As digital assets continue to gain popularity globally, including in rapidly growing markets like Vietnam, understanding robust security frameworks is essential for ensuring the safety and compliance of crypto platforms.
Understanding HIBT Security Audit Methodology
The HIBT security audit methodology stands for Highly Integrated Blockchain Technology security audit framework. It provides a systematic approach to assess the vulnerabilities within cryptocurrency platforms and smart contracts. Important areas covered in the HIBT methodology include:
- Smart Contract Audits: Evaluating the security and functional efficiency of deployed smart contracts.
- Tokenomics Analysis: Scrutinizing the economic models of cryptocurrencies to ensure their sustainability.
- Compliance Checks: Ensuring adherence to regional regulations and standards, especially relevant for markets like Vietnam.
- Penetration Testing: Conducting real-world simulated attacks to identify exploitable vulnerabilities.
- Source Code Review: Comprehensive analysis of the source code for security loopholes.
Why is Audit Methodology Important?
With the increasing sophistication of cyber-attacks, it’s no longer sufficient to have security practices in place; they must be continuously evaluated and enhanced.
For example, in Vietnam, the user base for cryptocurrency platforms surged by approximately 40% between 2021 and 2023, creating an urgent need for compliance and security measures to protect users’ investments.
Let’s break it down further:
- Risk Management: Effective audit methodologies help identify potential risks before they become significant threats.
- User Trust: A platform that prioritizes security can enhance user confidence, directly impacting growth.
- Regulatory Compliance: Proper audits ensure compliance with local laws, reducing the risk of legal issues.
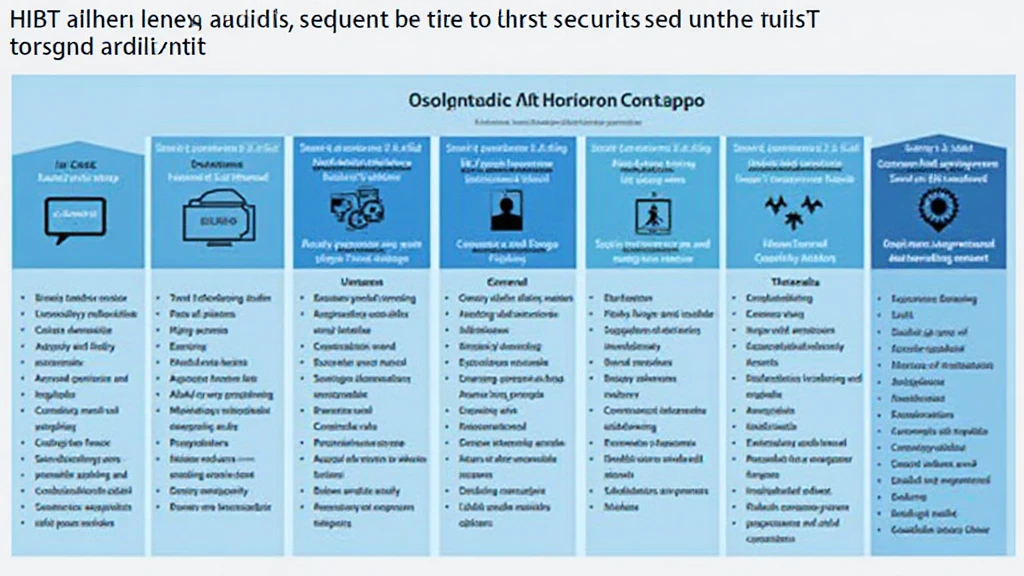
The Core Components of HIBT Methodology
The HIBT methodology sets itself apart with various structured components covering a wide spectrum of security checks:
1. Preliminary Assessment
Every audit should start with a preliminary assessment to understand the project, its architecture, and deployment environment. This phase allows auditors to gather initial data and prepare a tailored assessment strategy.
2. Intrusion Detection and Testing
Through methods akin to a bank vault’s security measures, auditors perform simulated intrusion efforts to detect potential breaches. This can significantly aid in identifying unexpected vulnerabilities.
3. Analyzing Smart Contracts
Smart contracts form the backbone of many crypto platforms. Thus, analyzing their functionality is critical. Auditors utilize specialized software tools to ensure contracts behave as intended under various conditions.
4. Comprehensive Reporting
Post-auditing, it’s crucial to prepare a clear and detailed report that outlines vulnerabilities alongside actionable recommendations. This promotes transparency and helps guide improvement efforts.
Best Practices for HIBT Audits
Implementing a successful auditing strategy goes beyond just adhering to the HIBT guidelines. Here are some best practices to consider:
- Regular Audits: Like routine maintenance for a car, regular audits ensure ongoing security and can adapt to emerging threats.
- Community Engagement: Engaging with the cryptocurrency community can offer insights into common vulnerabilities faced across the industry.
- Continuous Monitoring: Employ automated services to continuously monitor for vulnerabilities even post-audit.
Real-World Application of HIBT in Vietnam
As the Vietnamese crypto market expands, the application of the HIBT methodology is gaining traction. The rising user adoption of blockchain technologies calls for stringent security protocols.
For instance, local startups are prioritizing compliance with tiêu chuẩn an ninh blockchain to secure users’ digital investments while ensuring they are ready to meet future regulations.
Conclusion
In summary, adhering to the HIBT security audit methodology is crucial for any cryptocurrency platform aiming to safeguard user data and maintain a trustworthy ecosystem. Not only does it help in risk mitigation and compliance, but it also instills user confidence essential for growth—especially in emerging markets like Vietnam.
As the industry evolves, frameworks like HIBT are becoming indispensable in shaping the future of secure blockchain environments. For more information on the HIBT methodology and how to implement it effectively, check out hibt.com.
**Author:** Dr. Alex Nguyen, a leading expert in blockchain security with over 15 publications in the field and principal auditor for notable cryptocurrency projects worldwide.